Cybersecurity in Renewable Energy Systems
The Growing Threat Landscape in Renewable Energy
The Rise of Sophisticated Attacks
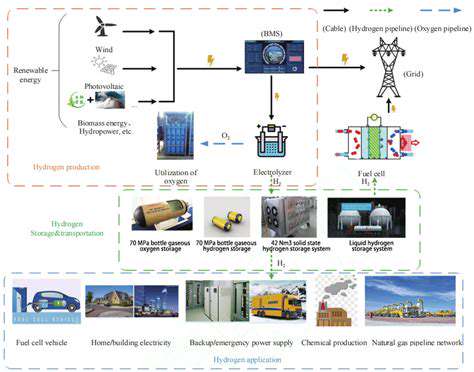
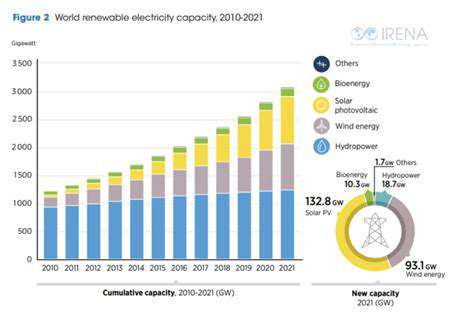
As the world shifts toward sustainable energy solutions, the renewable energy sector faces escalating cyber threats. These aren't just random hacking attempts but carefully orchestrated campaigns designed to cripple operations, steal proprietary data, and even cause physical harm to vital infrastructure. Attackers are finding weak spots in interconnected networks spanning smart grids, wind farms, solar arrays, and battery storage facilities. When one component fails due to compromise, the entire system risks a domino effect of failures.
Hackers are refining their methods to exploit renewable energy systems' unique weaknesses. Custom malware now targets SCADA systems, which manage energy distribution and core processes in these facilities. The proliferation of IoT devices in renewable energy operations adds another layer of vulnerability, creating more opportunities for breaches. This demands not only better security tools but also a cultural shift toward heightened vigilance among personnel.
Vulnerabilities in Supply Chains and Vendor Management
Renewable energy projects rely on sprawling supply chains with dozens of vendors and contractors—each a potential weak link. Cybercriminals can infiltrate these networks to access confidential data, tamper with equipment, or embed malicious code in components before deployment. Without rigorous vendor assessments and ongoing oversight, these risks remain unchecked.
Every supplier must follow strict security protocols, including thorough background checks, mandatory training, and frequent compliance audits. Securing the supply chain isn't just about protecting individual projects; it's about fortifying the entire renewable energy ecosystem against future attacks.
The Need for Enhanced Cybersecurity Measures
To combat these evolving threats, the industry must adopt a multi-layered defense strategy. This includes deploying advanced tools like intrusion detection systems, next-gen firewalls, and endpoint protection customized for renewable energy operations. Equally critical is training staff to recognize and respond to emerging threats.
Strong access controls, data encryption, and regular vulnerability scans are non-negotiable. Pair these with incident response plans to quickly neutralize breaches. Collaboration across industry players, governments, and security experts is key to sharing intelligence and developing effective countermeasures.
Protecting Critical Components of Renewable Energy Systems
Ensuring the Reliability of Solar Farms
Solar farms—with their vast networks of panels, inverters, and batteries—require ironclad security. Proactive cybersecurity measures must guard against unauthorized access, data theft, and operational sabotage. Implement strict authentication, encrypt sensitive data, and conduct frequent vulnerability tests. Neglecting these steps risks costly downtime and destabilizes the broader energy grid.
Attackers could manipulate solar farm outputs to cause grid fluctuations or steal financial data tied to projects. Robust defenses are the only way to ensure uninterrupted clean energy production.
Protecting Wind Turbine Infrastructure
Wind turbines depend on intricate control systems that hackers can exploit. Since these systems are interconnected, breaching one turbine could spread to others. Multi-factor authentication and real-time intrusion detection are essential, alongside regular software updates. Continuous monitoring of network traffic helps spot anomalies before they escalate.
Securing Energy Storage Systems
Battery storage systems hold massive energy reserves, making them prime targets. Compromised controls could trigger dangerous fluctuations or leaks of sensitive operational data. Encryption and strict access limits are critical safeguards.
Safeguarding the Grid Integration Infrastructure
Renewable energy's grid integration hinges on vulnerable communication networks. A single breach here could trigger blackouts. Secure protocols, access controls, and routine penetration testing are vital to prevent cascading failures.
Protecting Operational Data and Personnel
Sensitive data—like production metrics and maintenance logs—must be encrypted and tightly controlled. Staff training is equally crucial to thwart phishing scams. Strong passwords and multi-factor authentication should be standard practice for all personnel.
Addressing Supply Chain Vulnerabilities
With suppliers varying in cybersecurity maturity, vetting and ongoing audits are imperative. Clear security agreements and real-time monitoring of vendor networks reduce risks across the ecosystem.