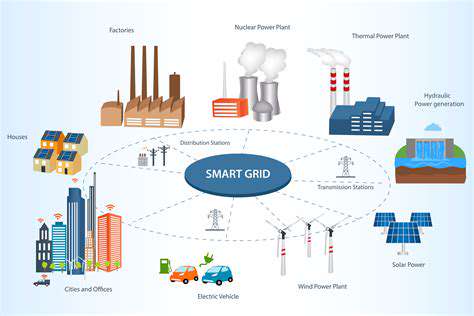
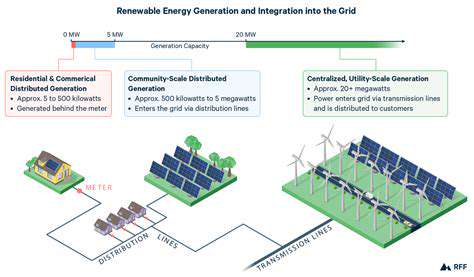
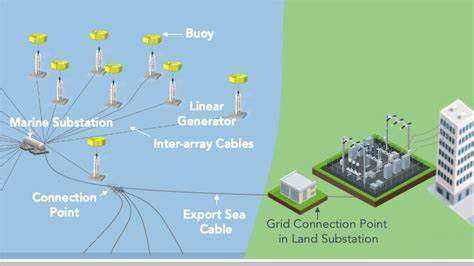
Cybersecurity in Renewable Energy Systems: Protecting the Grid
Strengthening Cybersecurity Defenses
Protecting critical infrastructure from cyberattacks requires a multifaceted approach that goes beyond simply installing firewalls. A robust cybersecurity strategy must encompass proactive measures, such as regular vulnerability assessments and penetration testing, to identify potential weaknesses before malicious actors exploit them. This proactive approach, coupled with robust incident response plans, ensures that organizations can quickly and effectively contain any breaches that may occur. Implementing strong access controls and multi-factor authentication is crucial to limit unauthorized access and protect sensitive data. Furthermore, educating employees about phishing scams and other social engineering tactics is essential to prevent human error from becoming a vulnerability.
Regular security awareness training for personnel is critical. This training should cover a wide range of topics, including identifying phishing emails, recognizing suspicious websites, and understanding the importance of strong passwords. By empowering employees with the knowledge and skills to recognize and report potential threats, organizations significantly reduce their risk profile. This proactive education also helps cultivate a security-conscious culture within the organization, fostering a collective responsibility for safeguarding critical infrastructure.
Collaboration and Information Sharing
Effective cybersecurity for critical infrastructure relies heavily on collaboration and information sharing between various stakeholders. This includes sharing threat intelligence among government agencies, private sector entities, and international partners. Rapid dissemination of information about emerging threats and vulnerabilities allows for timely mitigation strategies and helps prevent widespread attacks. Public-private partnerships can play a vital role in this process, fostering a collaborative environment where knowledge and resources are pooled to enhance overall cybersecurity posture.
Establishing clear communication channels and protocols is vital for rapid response to incidents. This includes pre-defined procedures for reporting and escalating security concerns. Having a well-defined incident response plan ensures that organizations can effectively contain and recover from cyberattacks, minimizing potential damage and downtime. This proactive approach, combined with a commitment to continuous improvement and adaptation to evolving threats, forms the bedrock of a truly comprehensive cybersecurity strategy.
Sharing best practices and lessons learned across different sectors and geographies is essential for strengthening overall cybersecurity. Regular knowledge exchange and benchmarking can help identify and address emerging vulnerabilities more effectively. This collaborative approach, which promotes the sharing of knowledge and resources, is crucial for strengthening the collective resilience of critical infrastructure against cyber threats.
International cooperation is also paramount. Cyber threats often transcend national borders, requiring coordinated efforts to address them effectively. International agreements and information-sharing mechanisms can significantly bolster the cybersecurity defenses of critical infrastructure worldwide. This global approach is vital to protecting interconnected systems and preventing the cascading effects of major cyberattacks.
Addressing the Challenges of Decentralization and Interconnectivity

Decentralization's Promise
Decentralization, at its core, promises a more equitable and transparent future. By distributing power and control across a network, it aims to reduce reliance on single points of failure and foster greater trust and accountability. This shift from centralized authorities to distributed systems holds immense potential for innovation and progress across various sectors.
The potential for increased security and resilience through redundancy is significant. Decentralized systems are inherently more resistant to censorship and single-point attacks, making them more robust in the face of adversity. This robustness is a key selling point, especially in a world increasingly vulnerable to cyber threats and geopolitical instability.
Challenges in Implementation
Despite the promise, the practical implementation of decentralized systems faces numerous challenges. Building and maintaining a secure and reliable distributed network requires significant technical expertise and resources, often exceeding the capabilities of individuals and small organizations. This barrier to entry can hinder widespread adoption.
Economic Incentives and Sustainability
Sustaining decentralized networks often requires innovative economic models, such as tokenized incentives and Proof-of-Stake mechanisms. These mechanisms need to be carefully designed to incentivize participation and ensure long-term sustainability. Furthermore, the economic viability of these systems is a critical factor in their widespread adoption.
Interoperability and Standardization
A key hurdle to the broader adoption of decentralized technologies is the lack of interoperability between different platforms and systems. The fragmented nature of existing decentralized ecosystems creates significant barriers for users seeking to seamlessly utilize different services and applications. Standardization efforts are crucial for unlocking the full potential of decentralized systems.
Scalability and Performance
Decentralized systems often face scalability challenges as their user base grows. Processing transactions and maintaining network integrity can become extremely demanding as the volume of data increases. Efficient solutions for scaling these systems are vital for their long-term viability and widespread adoption.
Security and Trust
Ensuring the security and trustworthiness of decentralized networks is paramount. The distributed nature of these systems necessitates robust mechanisms for verifying transactions, preventing fraud, and maintaining data integrity. Robust security protocols are essential for building user trust and fostering widespread adoption.
Governance and Regulation
The lack of a central authority in decentralized systems presents unique challenges related to governance and regulation. Establishing clear frameworks for decision-making, dispute resolution, and compliance with existing laws is crucial for mitigating risks and fostering a healthy environment for innovation. These decentralized systems need appropriate governance models to ensure the long-term success of these technologies.