Cybersecurity for Decentralization of Energy Generation Systems: Protecting Assets
Decentralized energy systems represent a significant paradigm shift from traditional centralized power grids. Instead of relying on large-scale power plants to generate and distribute electricity, decentralized systems leverage smaller, distributed energy sources, such as rooftop solar panels, wind turbines, and microgrids. This distributed approach offers numerous advantages, including enhanced resilience, improved energy access, and reduced reliance on fossil fuels.
This shift towards decentralization is driven by a growing recognition of the limitations and vulnerabilities of centralized energy infrastructure. Centralized grids are often susceptible to outages caused by natural disasters or other disruptions. Decentralized systems, by their very nature, are more resistant to such events, as they can operate independently and support each other in times of need.
Advantages of Decentralized Energy
One key advantage of decentralized energy is enhanced grid resilience. Smaller, distributed energy sources can compensate for outages in other parts of the system, ensuring continuous power supply to consumers. This resilience is crucial in areas prone to natural disasters or other disruptions that can knock out large sections of the traditional grid.
Furthermore, decentralized energy fosters a more sustainable approach to energy production. By leveraging renewable energy sources like solar and wind, these systems reduce reliance on fossil fuels and decrease greenhouse gas emissions. This, in turn, helps mitigate the effects of climate change and promotes a cleaner energy future.
Technological Advancements Driving Decentralization
Technological advancements are a major catalyst for the growth of decentralized energy. Innovations in energy storage solutions, particularly battery technology, are enabling the seamless integration of intermittent renewable energy sources like solar and wind. This allows for more reliable power generation and storage, which is crucial for the wider adoption of decentralized energy.
Challenges and Considerations for Implementation
While the benefits of decentralized energy are substantial, there are challenges that need careful consideration. One key challenge is the interoperability of different distributed energy resources and the need for robust communication infrastructure to manage and coordinate these systems.
Another crucial consideration is the integration of decentralized energy systems into existing power grids. A smooth transition requires careful planning and investment in new infrastructure to support the diverse range of energy sources and storage solutions that these systems employ.
Future Outlook and Implications
The future of decentralized energy looks promising, with continued advancements in technology and supportive policies likely to accelerate its adoption. This shift will likely lead to a more resilient, sustainable, and equitable energy system, benefiting both consumers and the environment.
The implications for energy markets and policy are also significant. Decentralization requires a re-evaluation of existing energy regulations and policies, and the potential for new business models and entrepreneurial opportunities will be substantial.
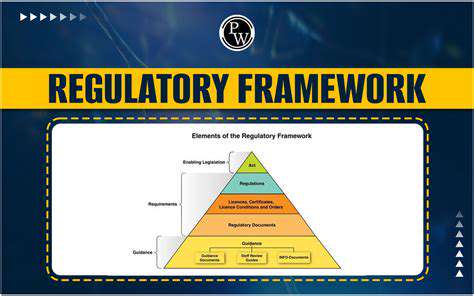
Identifying Vulnerabilities in Distributed Energy Resources (DERs)
Identifying Weaknesses in DER Communication Networks
Distributed Energy Resources (DERs) often rely on interconnected communication networks for control and data exchange. These networks, while crucial for efficient operation, can introduce significant vulnerabilities if not properly secured. The diverse range of communication protocols used across different DER components, from inverters to energy storage systems, can create a complex and potentially insecure ecosystem. Identifying the specific vulnerabilities within these communication channels, including potential weaknesses in encryption, authentication, and authorization mechanisms, is a critical first step in mitigating risks.
Assessing the Impact of Phishing and Malware Attacks
Cyberattacks targeting DERs can have far-reaching consequences, impacting not only the functionality of individual systems but also the broader grid stability. Phishing campaigns, designed to trick operators into revealing sensitive information or downloading malicious software, pose a significant threat. Malware infections can compromise DER control systems, leading to unauthorized access, data breaches, and even the potential for manipulating energy production and distribution.
Understanding the potential impact of these attacks is crucial for prioritizing security measures and developing effective incident response plans.
Analyzing Software and Firmware Vulnerabilities
The software and firmware embedded within DER components are often complex and frequently updated. However, these updates can introduce new vulnerabilities if not thoroughly tested and reviewed. Outdated or improperly patched software is a common vector for attackers. Identifying these vulnerabilities through rigorous code reviews, penetration testing, and vulnerability scanning is essential to ensure system integrity and prevent exploitation.
Evaluating Physical Security Measures for DER Components
While cybersecurity often focuses on digital aspects, the physical security of DER components should not be overlooked. Unauthorized access to equipment could enable attackers to tamper with hardware, gain physical control, or install malicious devices. Implementing robust physical security measures, such as access controls, surveillance systems, and environmental protection, is essential to complement digital security protocols. This includes protecting critical infrastructure such as solar panels, wind turbines, and energy storage facilities from physical intrusion.
Developing a Comprehensive Security Strategy for DER Integration
A holistic security strategy is necessary to address the multifaceted threats facing DERs. This strategy should encompass all aspects of the DER lifecycle, from design and implementation to operation and maintenance. It should involve regular security assessments, penetration testing, and vulnerability management. Furthermore, ongoing training for personnel on cybersecurity best practices is crucial to ensure that all stakeholders understand and implement security protocols effectively. A strong security strategy will also incorporate incident response plans and procedures to deal with potential attacks.
Implementing Robust Cybersecurity Measures for DERs

Understanding the Cybersecurity Landscape
In today's interconnected digital world, cybersecurity is no longer a luxury but a critical necessity for organizations of all sizes. The constant evolution of cyber threats, from sophisticated ransomware attacks to increasingly sophisticated phishing campaigns, demands a proactive and robust approach to safeguarding sensitive data and systems. Understanding the current threats and vulnerabilities is the first step in developing an effective defense strategy. This includes recognizing the various attack vectors, such as malware, social engineering, and vulnerabilities in outdated software, to fortify defenses against these evolving threats.
Cybersecurity threats are multifaceted and ever-changing. Staying informed about emerging threats and adapting security measures accordingly is crucial. This involves continuous monitoring, analysis, and adaptation to the dynamic nature of the cybersecurity landscape. A proactive approach to cybersecurity involves more than just reactive measures; it requires a comprehensive understanding of the potential risks and the development of strategies to mitigate them.
Developing a Comprehensive Security Strategy
A robust cybersecurity strategy is not a one-size-fits-all solution. It requires careful consideration of the specific needs and vulnerabilities of an organization. Factors such as the type of data handled, the size and structure of the organization, and the potential impact of a security breach must be meticulously evaluated. This detailed assessment should form the foundation of a multi-layered security architecture.
Key components of a comprehensive security strategy include strong access controls, regular security audits, and employee training programs. Implementing these components can significantly reduce the risk of successful attacks and protect sensitive information. These measures are vital in preventing unauthorized access and protecting valuable data assets. A robust strategy also needs to consider the incident response plan in order to effectively manage and mitigate the impact of any potential breaches.
Implementing and Maintaining Security Controls
Implementing robust security controls is not just about installing software; it's about creating a culture of security awareness within the organization. This includes educating employees about phishing scams, password security best practices, and the importance of reporting suspicious activity. Effective security controls are critical to deterring and mitigating cyber threats.
Regular security updates and patching of software vulnerabilities are essential to maintain a strong defense. This proactive approach helps to prevent exploitation of known weaknesses in systems and applications. Regular security audits and penetration testing are crucial to identify and address any vulnerabilities that may have slipped through the cracks. These assessments provide critical insights and help to fine-tune security measures for optimal protection.
Monitoring and Responding to Threats
Continuous monitoring of network activity and system logs is vital for detecting potential security breaches in real-time. This proactive approach allows for the rapid identification and response to threats, minimizing the potential damage. Implementing intrusion detection and prevention systems (IDS/IPS) can further bolster security posture.
Developing and regularly testing incident response plans is critical. These plans should outline procedures for handling security incidents, including containment, eradication, and recovery. Effective communication and collaboration between teams are essential to ensure a swift and effective response to any security breach. A robust incident response plan is essential for minimizing the impact of any security breach.
Collaboration and Standardization for Enhanced Security

Defining Collaboration in the Modern Workplace
Collaboration, in the modern workplace, transcends simple teamwork. It encompasses a dynamic interplay of individuals and teams, leveraging diverse skills and perspectives to achieve shared goals. Effective collaboration necessitates clear communication channels and a shared understanding of objectives. This often involves leveraging technology and fostering a culture of trust and open dialogue, enabling individuals to contribute their expertise without fear of judgment.
Furthermore, collaboration in a modern context demands adaptability and flexibility. Teams must be prepared to adjust strategies and approaches as circumstances evolve. This responsiveness is critical to achieving project success in today's rapidly changing business environment.
The Role of Standardization in Business Processes
Standardization in business processes is paramount for efficiency and consistency. By establishing clear protocols and procedures, organizations can streamline workflows and reduce errors. This, in turn, leads to improved productivity and a more predictable outcome for projects and tasks.
Standardized processes also foster better knowledge transfer and skill development within teams. Employees can learn from each other more effectively when operating within a common framework, ultimately enhancing overall organizational performance.
Enhancing Communication for Seamless Collaboration
Effective communication is the lifeblood of successful collaboration. Clear and concise communication ensures that everyone understands the project goals, individual responsibilities, and expectations. This proactive approach to communication helps prevent misunderstandings and minimizes the risk of conflict.
Furthermore, utilizing various communication tools, such as project management software, instant messaging platforms, and video conferencing, allows teams to stay connected and informed in real-time. This technology-driven approach to communication enables seamless and efficient collaboration across geographical boundaries.
Implementing Standardized Communication Protocols
Implementing standardized communication protocols establishes a common language and structure for all interactions within a team or organization. This ensures that everyone is on the same page, reducing ambiguity and facilitating smoother information exchange. Standardized protocols also contribute to increased efficiency by minimizing the time spent on clarifying communication points.
Leveraging Technology for Enhanced Collaboration and Standardization
Technology plays a crucial role in driving both collaboration and standardization. Project management software, communication platforms, and shared document repositories empower teams to work together seamlessly, regardless of location. The availability of such tools significantly improves the efficiency and effectiveness of collaborative efforts.
Furthermore, these technologies facilitate the implementation of standardized processes. By automating tasks and tracking progress, organizations can ensure consistency and accuracy, leading to improved quality and reduced operational costs.
Measuring the Impact of Collaboration and Standardization
Measuring the impact of collaboration and standardization initiatives is essential for demonstrating their value and identifying areas for improvement. Key performance indicators (KPIs) such as project completion rates, error rates, and employee satisfaction levels can provide valuable insights into the effectiveness of these strategies. By tracking these metrics, organizations can make data-driven decisions to optimize their approaches to collaboration and standardization.
Regularly evaluating the outcomes of these initiatives is critical for continuous improvement. This iterative approach allows for adjustments and refinements to maximize the benefits of collaborative and standardized processes.